As we wrap up October, a.k.a. Cybersecurity Awareness Month, we want to discuss phishing scams and the harmful impact they can have on your organization.
What is phishing?
Quite simply, phishing is when nefarious individuals prey on people by using deceitful tactics to defraud them. It could be that they want to take your money. It could be for stealing information and corporate espionage. It could even be someone who wants to get revenge, either on you or your organization, for whatever reason.
Do phishing scams really work?
It is doubtful that this is a new topic for most people. In fact, your organization has probably held meetings, sent out alerts, and possibly even sent out fake phishing emails just to see if you’ve been paying attention. So why is there so much attention paid to this topic? And since so many people are aware of them, do they really work? In short, yes.
The Anti-Phishing Working Group (APWG) recorded 1,025,968 phishing attacks in the first quarter of 2022 alone, the worst quarter ever observed. According to the FBI, criminals have stolen $12 billion (with a B!) from companies over five years. One wrong click on a bad link could result in a significant cost to your organization. It could be through a ransomware attack where a hacker threatens to publish your data unless they are paid a ransom. It could be through the loss of trust by your donors knowing that your organization and all your data was compromised. It could be the time and money that must be invested to fix and overcome the attack.
How Does it Work?
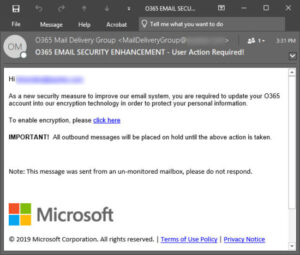
One example of a phishing email would be an email that appears to be sent from a reputable person or organization. One thing that seems to be consistent is that there is some call to action with a sense of urgency; you need to enable something, you need to pay an outstanding debt, you need to update your password, etc.
In the example above, it appears that this email is sent by Microsoft. The email address is O365 (for Office 365), and it has the Microsoft logo and even a copyright notice at the bottom. The urgent message is that you need to enable encryption, or all outbound messages will be placed on hold. If you click on the link, it doesn’t automatically say, “Ha! We got you. Now give us money.” Hackers are much craftier than that. Instead, it takes you to a landing page that looks eerily similar to the actual Microsoft login page. The difference is, when you enter your login information, it doesn’t log you into Microsoft but sends your credentials to those who intend to do harm to you or your organization.
The Human Firewall
Your organization may feel protected. Whether your IT department is internal or external, hopefully your IT support includes protection software and patch management, but even that can’t protect against every threat. Connect Cause Chief Technology Officer Paul Bender says, “The human firewall is the last line of defense and really the best line of defense against phishing.”
By training ourselves, and our employees, our organizations are better protected in the case of an attack. And an attack WILL happen. Nearly every organization will be hacked or targeted at some point. Most of the time it is not a matter of if you will be hacked, but when, and how impactful the incident will be.
How to Detect a Phishing Email
Back to our example from before, if you were to get that exact email, would you be able to figure out that it is a phishing attempt and not a legitimate email from Microsoft? Here are a few tips and things to look out for any time you are opening an email or clicking on a link—even if it seems to be from a reputable source.
- Start at the top, is the sender’s address legit? We aren’t talking about the fact that O365 Mail Delivery Group could be real. What does the actual email address look like? Many times, it is MailDeliveryGroup@fowin3werjc8w.oaernwerod.org. If it looks funny, be extra careful.
- Who is the email to? If you are being asked to do something urgently, how are you addressed in the email? Is it to “client” or “user” or does it have your real name?
- What is the call to action? Is the request something that you would normally be asked to do? In the case of the example, if you don’t usually get asked to enable encryption for Connect Cause, it should raise a red flag if to get this email. Maybe the email is from your CEO asking you to pay an invoice. Do you normally get asked to do that? If not, that should alert you that something is off.
- Is it sent with high importance? Just like with the call to action, hackers want to send you into a panic thinking that something is urgent, and the success of your organization depends on you acting quickly.
- Double-check all links. Regardless of whom the email comes from, it is always a good idea to double-check a link before you click on it. Just hover over it and make sure that a link that is supposed to go to connectcause.com ACTUALLY goes to connectcause.com.
- Read the email carefully. Are there typos, incorrect punctuation, or maybe weird capitalization patterns? Oftentimes these can alert you that the email is a scam.
Beyond the Human Firewall
While the human firewall is a great line of defense, humans are not perfect, and when it comes to dealing with security risks there is no single silver bullet solution that can detect and prevent all attacks.
Nonprofits require comprehensive solutions that promote security for their crucial data. With a multi-layered approach, the risk of data loss and theft can be exponentially reduced.
On the technical side, one thing your organization can do is use a reputable cloud email provider. There are great tools available, but you need to be using a business email. It can be tempting to use a Gmail or Hotmail account to save costs, but those accounts don’t offer any layer of spam or email-borne attack protection and it may prove more costly in the long run.
Other options include using a comprehensive spam filtering service such as AppRiver, Zix, or Barracuda, and implementing multi-factor authentication. Let’s say you fell victim to the example above and gave away your login credentials. With MFA, they won’t get far, and you may be alerted that they are trying to use your information.
We also highly recommend that you partner with a cybersecurity awareness and engagement system. Whether that is for the additional cybersecurity protection, or just to keep everything running smoothly so that you can focus on the people in front of you instead of the technology, a good IT partner is also going to be able to provide the cybersecurity awareness training for you.
Some of the ones that our experts suggest are:
These cybersecurity awareness trainings can poke and prod into your organization to find your weaknesses and allow you to fix them before those who mean harm find them.
If you want to learn more about Phishing and the Human Firewall, check out or Lunch & Learn broadcast with Connect Cause Chief Technology Officer Paul Bender.
If you still have questions or worry that your nonprofit organization is at risk, schedule your complimentary tech assessment today to find out where and if you’re organization is vulnerable.
—www.ConnectCause.com—



